Jan 17, 2025
DNA Nanorobots Unlock New Frontiers in Targeted Drug Delivery
Posted by Saúl Morales Rodriguéz in categories: bioengineering, biotech/medical, genetics
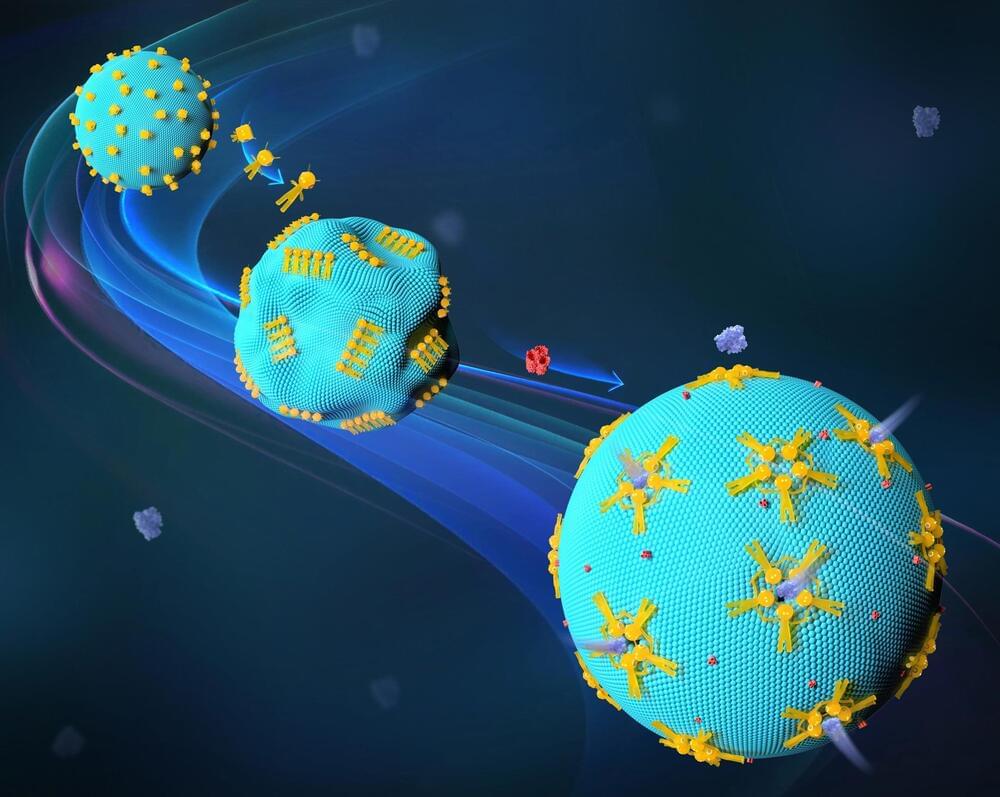
Scientists develop DNADNA, or deoxyribonucleic acid, is a molecule composed of two long strands of nucleotides that coil around each other to form a double helix. It is the hereditary material in humans and almost all other organisms that carries genetic instructions for development, functioning, growth, and reproduction. Nearly every cell in a person’s body has the same DNA. Most DNA is located in the cell nucleus (where it is called nuclear DNA), but a small amount of DNA can also be found in the mitochondria (where it is called mitochondrial DNA or mtDNA). tabindex=0 DNA nanorobots capable of modifying artificial cells.