Jan 17, 2025
Quantum engineers ‘squeeze’ laser frequency combs to make more sensitive gas sensors
Posted by Saúl Morales Rodriguéz in categories: biotech/medical, quantum physics
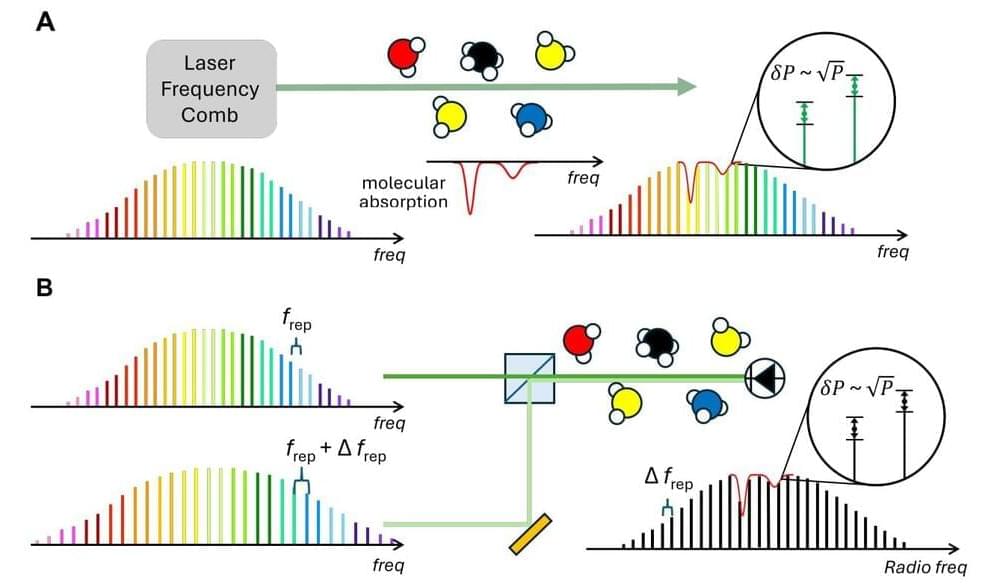
For the first time ever, scientists have used a technique called “quantum squeezing” to improve the gas sensing performance of devices known as optical frequency comb lasers. These ultra-precise sensors are like fingerprint scanners for molecules of gas. Scientists have used them to spot methane leaks in the air above oil and gas operations and signs of COVID-19 infections in breath samples from humans.
Now, in a series of lab experiments, researchers have laid out a path for making those kinds of measurements even more sensitive and faster—doubling the speed of frequency comb detectors. The work is a collaboration between Scott Diddams at CU Boulder Boulder and Jérôme Genest at Université Laval in Canada.
“Say you were in a situation where you needed to detect minute quantities of a dangerous gas leak in a factory setting,” said Diddams, professor in the Department of Electrical, Computer and Energy Engineering. “Requiring only 10 minutes versus 20 minutes can make a big difference in keeping people safe.”